About the product
About the product
Microsoft Sentinel or Azure Sentinel ( since it’s inside Azure ) is a cloud-based security platform that allows businesses to detect and respond to security threats in real time. It analyzes data from various sources, including network traffic, user activity, and third-party security tools, using advanced machine learning and automation.
Sentinel gives security teams a centralized view of the organization’s security posture, allowing them to quickly identify and respond to potential threats. It also has incident management and response capabilities, allowing teams to investigate and resolve security incidents.
Examine Microsoft Cybersecurity Reference Architectures to see how this critical product addresses cloud cybersecurity.
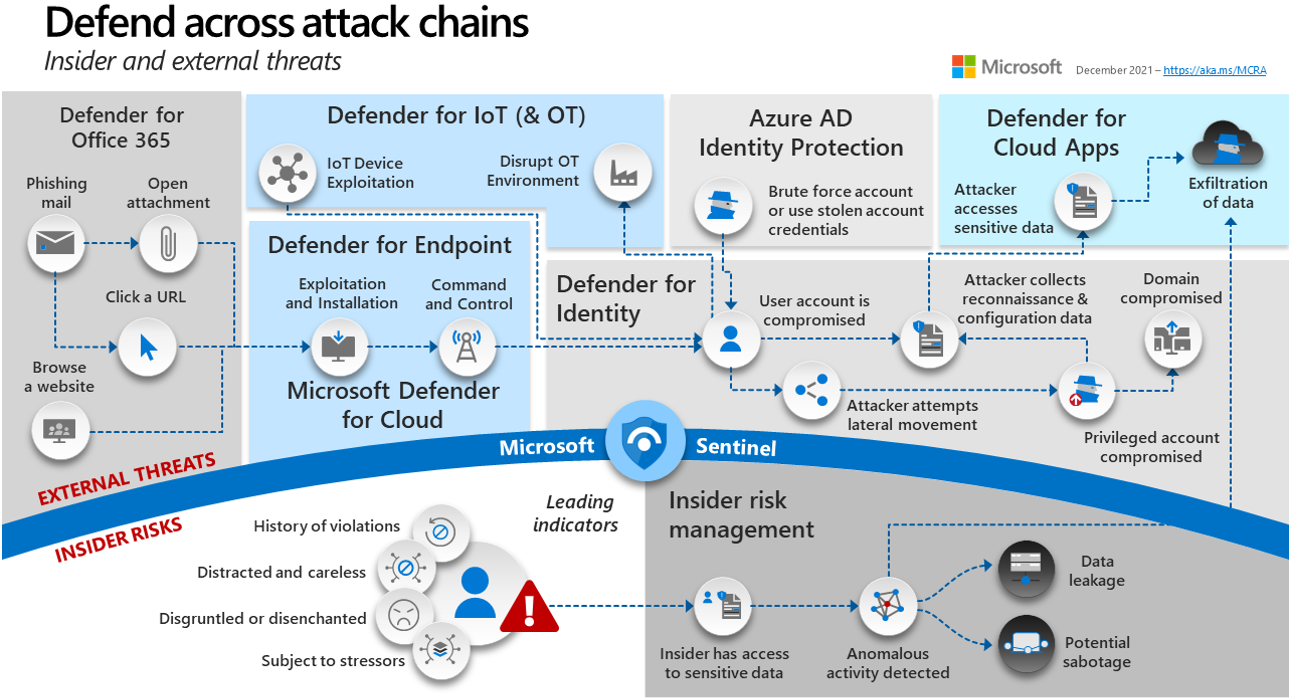
Let us now go over some of the item’s key components.
Sentinel Workbooks
A workbook is a powerful tool in Microsoft Sentinel that allows security teams to analyze and investigate security incidents in real time. Workbooks are pre-built, interactive dashboards that provide a centralized view of an organization’s security posture and enable security teams to identify and respond to potential threats quickly.
Each workbook is customized for a particular use case, such as threat hunting, incident investigation, or compliance reporting. A threat hunting workbook, for example, would allow you to search and analyze data from various sources, such as network traffic, user activity, and security logs, in order to identify potential threats. An incident investigation workbook would allow you to look into a specific incident and view relevant data, such as alerts, logs, and network traffic, all in one place.
Sentinel workbooks are highly customizable, allowing security teams to tailor them to their organization’s specific requirements. They can be used to build custom views, visualizations, and queries, as well as integrate with third-party security tools for more data and context.
Sentinel Playbooks
Workbooks in Sentinel also include “playbooks,” which are pre-built workflows that automate common incident response tasks like data collection, analysis, and remediation. This enables security teams to respond to incidents in a more timely and efficient manner.
Playbooks are a key feature of Sentinel that assist in the detection and investigation of potential threats.
Analytics Rules
Another key feature, Analytics rules detect and alert on specific security events or behavioral patterns. These rules are built on machine learning algorithms and are intended to detect known security threats like malware or suspicious network activity.
They can also be used to detect potential insider threats such as data theft or unauthorized use of privileged accounts. When a rule is triggered, an alert is generated that a security analyst can investigate.
Hunting
Hunting works similarly to rules, but with manual triggers rather than the event-based analytics rules.
Having said that, Hunting enables security teams to search for and identify unknown or emerging threats on demand. Sentinel’s hunting capabilities are built on the ability to query and analyze large amounts of security data from a variety of sources, including network traffic, user activity, and security logs. This enables security teams to identify behavioral patterns and anomalies that may indicate a security threat.
Together, analytics rules and hunting provide a powerful combination for detecting and investigating potential threats.
There is more to learn..
In summary, Sentinel includes a variety of security tools, security information and event management (SIEM), threat intelligence, and security automation.
These tools work in tandem to provide a comprehensive security solution that assists organizations in protecting themselves against cyber threats.
Go on!
Implement Microsoft Sentinel right now. 🍀
